Obscure DNSSEC Pitfalls: DS Record Propagation Delays in Multi-Registrar Domain Setups Published: 17 Jul, 2025
Obscure DNSSEC Pitfalls: DS Record Propagation Delays in Multi-Registrar Domain Setups
When managing domain security through DNSSEC (Domain Name System Security Extensions), most registrants focus on key generation, rollover timing, and cryptographic integrity. But one often-overlooked vulnerability lurks not in the cryptography itself, but in the operational nuance of multi-registrar setups and the propagation behavior of Delegation Signer (DS) records.
This post explores one of the most obscure and rarely documented failure modes in DNSSEC deployments: DS record propagation delays or silent overwrites in domains registered across multiple registrars with overlapping authority, particularly in ccTLDs and legacy gTLDs with liberal delegation policies.
Why DS Records Matter More Than You Think
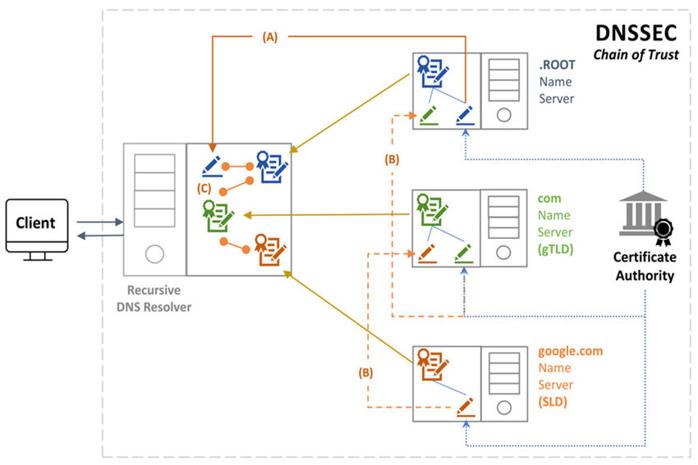
A DS record links a domain’s DNSKEY to the parent zone, acting as a cryptographic bridge in the chain of trust. If your DNSKEY changes (e.g., during key rollover) but the DS record isn’t updated promptly at the parent, resolvers will see a broken chain and fail validation—rendering the domain unreachable.
In standard setups with one registrar, this is a simple API call or web panel update. But when multiple registrars have edit access to the same domain (yes, this happens), or when registry-side automation inconsistently applies DNSSEC metadata, DS propagation becomes a silent killer.
The Niche Use Case: Multi-Registrar, DNSSEC-Enabled Domains
Although ICANN’s Registry-Registrar model assumes one active registrar per domain, real-world exceptions include:
-
Domains under shared reseller/registrar accounts.
-
ccTLDs that allow direct registry interaction alongside registrar interfaces.
-
Legacy registrar lock-in where transfer locks are active but DS updates are possible via a secondary control panel.
In these cases, multiple actors may be capable of submitting DS records—leading to:
-
Stale DS entries remaining after DNSKEY rollover.
-
Delayed DNSSEC validation errors as DNSKEYs expire but parent zones retain invalid DS hashes.
-
Propagation race conditions, where the “last DS push” wins, potentially restoring outdated records.
A Real (Obscure) Example
Consider the .cm TLD (Cameroon), where the registry permits direct interaction via EPP and also supports delegated registrar management. A domain under DNSSEC with keys rotated via registrar A may have DS entries overwritten by registrar B if:
-
Registrar B uses an outdated template or cached DS configuration.
-
A scheduled sync job on registrar B’s system pushes legacy DS data back to the registry.
-
The registry doesn’t validate DS record freshness or cryptographic alignment.
The result? A “signed but bogus” DNSSEC state, and complete resolution failure on validating resolvers (e.g., Google Public DNS, Cloudflare 1.1.1.1).
How to Detect and Prevent This
Detection
-
Use
dig +dnssec yourdomain.tldand validate the chain manually. -
Query parent DS records from multiple public resolvers to compare:
dig DS yourdomain.tld @a.gtld-servers.net dig DS yourdomain.tld @1.1.1.1 -
Monitor DNSViz and Zonemaster for propagation anomalies.
Prevention
-
Enforce exclusive DS record control via registrar lock or registry-side ACLs.
-
Automate DS push with atomic rollovers, preferably using RFC 8078 (CDS/CDNSKEY signaling).
-
Avoid registrars that cache DS records or lack clear DNSSEC APIs.
-
Periodically audit parent zone DS entries against your active DNSKEYs.
Final Thoughts
This edge case doesn’t apply to 99.9% of DNSSEC users. But for infrastructure providers, SaaS vendors, or security-focused registrants managing high-availability domains across registrars, this kind of silent DNSSEC misconfiguration can become a costly and invisible failure.
We recommend building periodic integrity checks into your DNS pipeline, and treating DS record hygiene as seriously as TLS certificate expiration.